If you are not being informed about “DoS and DDoS,” we want you to read the discussion below! First of all, DoS vs DDoS attacks are other types of cyberattacks. Yes! Cyberattacks are a real thing.
They’re also more common than you think and can happen to anyone. In fact, according to the National Cyber Security Alliance (NCSA), over 1 in 5 Americans have been victims of cybercrime in their lifetime.
According to research , the average DDoS attack in the second quarter of 2022 utilized 5.17 Gbps of data, a slight increase from the previous year. However, while this is sufficient to cripple most small to medium-sized websites, it is significantly lower than the average for the first quarter of 2021, which is 9.15 Gbps.
Cyberattacks are attacks on systems that use computers and the internet. These attacks can be carried out by using different methods, and some of them are mentioned below:
- Malware is a cyberattack that installs on a computer and tries to make it do things the user doesn’t want it to do. It could take over your computer or send you spam.
- Phishing is a cyberattack that tries to get you to give away your personal information by pretending to be from a legitimate company (like your bank). It usually comes in an email or text with an offer for something free, like a fake credit card or gift card number. Use PowerDMARC’s anti-phishing solutions to be safe from such attacks.
- Social engineering is an attack that involves obtaining confidential information through deception. In this case, the attacker gains access to a system by tricking someone into giving them sensitive information.
DoS vs DDoS: An Overview
DoS and DDoS attacks are two different types of cyberattacks.
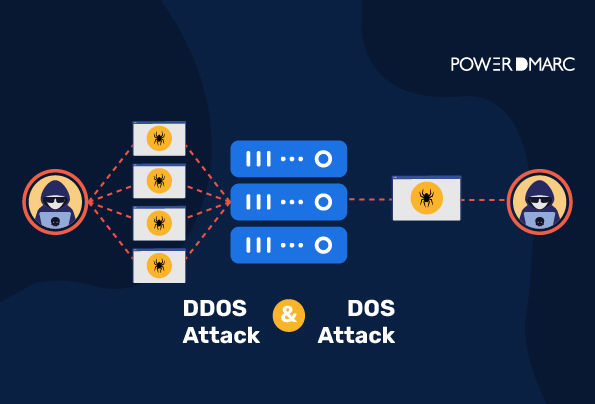
- A DoS (denial of service) attack is the fastest-growing type of cyber attack where the attacker sends malicious files to a system, making it unusable. An attacker can perform this attack using a single computer or device to launch the DoS attack.
- A distributed denial of service (DDoS) attack is when an attacker sends a flood of traffic to multiple systems simultaneously. An attacker can launch this attack from many distributed sources.
What Is the Difference Between a DoS and a DDoS Attack?
DoS attacks send a large amount of traffic to a victim’s computer, shutting it down. DoS attacks are used in online environments—such as websites—to make them unavailable for users by either crashing or overwhelming the server. This attack overloads a website’s server by sending large amounts of traffic.
A distributed denial-of-service (DDoS) attack involves sending massive amounts of traffic to a single website from many different sources, making it difficult for legitimate users to access that site.
Difference Between DoS and DDoS;
DoS Attack
- Denial of service attacks, or DoS for short, attempt to make a computer resource unavailable by flooding it with requests.
- In a DoS attack, one system sends malicious stuff to the victim system.
- The victim’s computer is funded from the bundle of harmful data sent from a single location.
- This type of attack is slower than DDoS.
- The software can block DoS quickly because one system is being used.
- With DoS tools, the attacker targets the victim’s device with a single system.
- DoS Attacks have become easier to trace.
DDoS Attack
- Distributed denial of service attacks, or DDoS for short, attempt to make a computer resource unavailable by flooding it with requests from multiple resources.
- Multiple systems send malicious stuff to the victim system in a DDoS attack.
- In the DDoS and DoS difference, the DDoS attacker makes the victim’s computer funded from the bundle of harmful data sent from multiple locations.
- This attack is faster as compared to the DoS attack.
- A DDoS attack is brutal to block easily, as the attacker sends data from more than one device.
- The attacker uses volumeBots to attack the victim at the same time.
- These attacks can’t be traced easily.
How To Prevent DoS and DDoS Attacks?
Here is the good news! You can prevent DoS and DDoS attack if you correctly follow the protection strategy. The threat of a DoS attack to modern organisations is constant, but you can avoid it yourself before and after an attack. It’s important to realise before following a protection strategy that you can’t stop every DoS attack that targets your system. However, the chances are that you can minimise the damage from a successful attack while implementing a strategy.
The key to minimising the damage caused by incoming attacks is to do the following:
- Network Monitoring
- Test Run DoS Attacks
- Strategy
Network Monitoring
When you monitor your traffic, you’ll be able to take action if you see unusual data traffic or an unknown IP address. You can detect these minor signs early by monitoring your network traffic and keep your service online by avoiding unexpected downtime costs. Also, constant network monitoring can see harmful vibes before it attacks the victim.
Test Run DoS Attacks
It is impossible to prevent every DoS attack, but you can prepare yourself once an attack occurs. Simulating DDoS attacks against your network is one of the easiest ways. By simulating an attack, you can test out your current prevention methods and develop some real-time prevention strategies to save money (ransomware) in the event of an attack.
Strategy
Having a strategic plan ready to handle damage control in case an attack occurs can make or break an attack. It is important to assign roles to team members, who will be responsible for responding to attacks once they happen.
A clear and fully approved strategic plan can make a huge difference between an inconvenient attack and a devastating one. It also includes setting guidelines for customer support so that customers aren’t left devasted while you resolve technical issues.
Conclusion
Only a professional service can provide reliable and effective DDoS protection. The provider will handle all possible risks connected with the attack and defend your assets from illegal hacking.
DoS and DDoS attacks are carried out for various reasons, ranging from political gain to financial gain to the outperformance of companies. DDoS attacks are faster than DoS attacks because they use multiple systems, whereas DoS attacks involve a single system and are slower.
Protect your system from malicious files and harmful data in the case of DoS vs DDoS attacks that damage your system and demand a huge (ransom).
- Rise in Tax Scams and IRS Email Impersonation Attacks During Tax Season - May 2, 2024
- Email Safety 101 to Fight Crypto Scams - April 30, 2024
- How to Find the Best DMARC Solution Provider for Your Business? - April 25, 2024