Key Takeaways
- DMARC is an essential email authentication protocol that helps protect domains against phishing and spoofing.
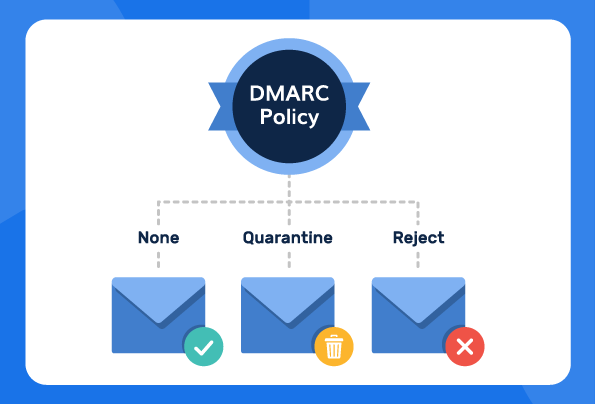
- There are three DMARC policy types: None, Quarantine, and Reject, each offering a different level of enforcement.
- Implementing DMARC policy allows organizations to safeguard their brand, employees, and customers from damaging email-based threats.
- Global cybercrime losses are projected to top US$10.5 trillion in 2025, emphasizing the scale of the threat.
In early 2024, Google and Yahoo made it clear that all bulk senders must have DMARC policy in place. This requirement turned DMARC policy configuration from a routine technical step into an urgent priority for organizations of every size. After the announcement, teams began reviewing, updating, and enforcing their DMARC policies to meet the new standards, prevent deliverability issues, and reduce the risk of domain misuse as email threats continued to grow.
Setting the right policy helps organizations protect their brand, employees, and customers from impersonation attempts. And while a DMARC policy alone can’t solve every email security challenge, it remains one of the most effective defenses against phishing and spoofing attacks.
In this article, we explore DMARC policy, how to implement it, the challenges and benefits, and why you should opt for our hosted DMARC solution for policy implementation.
What is a DMARC Policy?
DMARC policy is an email validation system that uses Domain Name System (DNS) to instruct receiving mail servers on how to handle emails claiming to be from your own domain but failing authentication checks. It is denoted by the “p” tag in the DMARC record that specifies the action mail servers should take if an email fails DMARC validation.
A properly implemented policy allows you to decide how strictly email providers should treat messages that don’t pass authentication. To put it simply, you choose the level of enforcement you want applied to suspicious or unauthorized emails.
You can set your policy to:
- Let it through anyway (p=none)
- Flag it as suspicious (p=quarantine)
- Block it completely (p=reject)
The p= tag in your DMARC record is what controls this behavior. It tells receiving servers which enforcement level to apply, making it one of the most important parts of a DMARC setup. A stricter policy like p=reject gives you the strongest protection by preventing spoofed or unauthorized emails from being delivered.
The 3 DMARC Policy Options
Before choosing a policy, it helps to understand what each option does and how it affects the way your domain is protected.
The three DMARC policy types include:
1. DMARC policy: None (p=none)
DMARC policy none (p=none) is a relaxed mode that triggers no action on the receiver’s side. This policy can be used to monitor email activity and is typically used during the initial DMARC implementation phase for monitoring and data collection.
It doesn’t provide any level of protection against cyberattacks and allows all messages to be delivered, regardless of authentication results. This option is specified in the DMARC record using the “p=none” tag.
Example: v=DMARC1; p=none; rua= mailto:(email address);
When to use p=none
- Use this policy when you want to monitor your email traffic before enforcing DMARC.
- Ideal for domains that are still identifying all legitimate sending sources.
- Receiving mail servers take no action on failing messages; emails are still delivered.
- You continue to receive DMARC aggregate reports, helping you understand authentication issues before moving to stricter policies.
2. DMARC policy: Quarantine (p=quarantine)
This option is specified in the DMARC record using the “p=quarantine” tag. p=quarantine provides some level of protection as the domain owner can prompt the receiver to roll back emails into the spam or quarantine folder to review later in case DMARC fails.
This policy instructs the receiving mail server to treat messages that fail DMARC authentication with suspicion. It is often implemented as an intermediate step between “none” and “reject”.
Example: v=DMARC1; p=quarantine; rua=mailto:(email address);
When to use p=quarantine
- Use this policy when you want stronger protection but still need to review suspicious emails before fully blocking them.
- Failing messages are sent to the spam/junk folder, giving you a chance to inspect them without losing legitimate mail.
- Acts as an intermediate enforcement level, helping you transition smoothly toward p=reject.
- Allows you to evaluate the impact of DMARC and decide whether flagged emails are legitimate or should be discarded.
- Helps reduce inbox clutter by keeping questionable emails out of the main inbox, while still allowing visibility.
3. DMARC policy: Reject (p=reject)
This option is specified in the DMARC record using “p=reject”. This is the strictest policy, telling receivers to reject unauthenticated messages.
DMARC policy reject provides maximum enforcement, ensuring messages that fail DMARC checks are not delivered at all. The policy is implemented when domain owners are confident in their email authentication setup.
Example: v=DMARC1; p=reject; rua= mailto:(email address);
When to use p=reject
- Choose this policy when you want the highest level of protection against phishing, spoofing, and any unauthorized use of your domain.
- Emails that fail authentication are fully blocked, ensuring suspicious messages never reach recipients.
- Best for domains that are already fully authenticated across all sending services and no longer need to quarantine borderline cases.
You should:
- Test thoroughly and confirm all legitimate senders pass SPF and DKIM before moving to p=reject.
- Keep DMARC reporting enabled so you can monitor any remaining failures and ensure everything continues to run smoothly.
- For a safe rollout, start at p=none, move to p=quarantine, and then advance to p=reject once your reports show consistent alignment.
Other DMARC policies
DMARC offers additional policy parameters to fine-tune implementation.
- The percentage (pct=) parameter allows gradual policy rollout by specifying the portion of messages subject to DMARC. For example: pct=50 applies the policy to 50% of messages.
- When to use it:
- Use pct= when you’re transitioning from p=none → p=quarantine → p=reject and want to test enforcement in stages without impacting all outgoing mail.
- Timeline guidance:
- Start with pct=20 during early testing.
- Increase to pct=50–70 when most legitimate senders are passing authentication.
- Move to pct=100 once you’re confident your setup is stable.
- When to use it:
- The subdomain policy (sp=) is a policy record that sets separate rules for subdomains. It is useful when subdomains require different handling. For example: v=DMARC1; p=reject; sp=quarantine; rua=mailto:dmarc-reports@example.com.
- When to use it:
- Use sp= when your subdomains have different sending behaviors or when you want stricter or more lenient enforcement compared to your primary domain.
- Timeline guidance:
- Apply sp=none while evaluating subdomain senders.
- Switch to sp=quarantine once you verify their authentication.
- Move to sp=reject when you no longer want subdomains misused for spoofing.
- When to use it:
Setup DMARC Policy the right way with PowerDMARC!
Why DMARC Matters
Emails can be easily forged, making it hard to tell the real deal from a dangerous fake. That’s where DMARC comes in. DMARC is like an email security checkpoint that verifies the sender’s identity before letting messages through, and it plays a critical role in achieving regulatory compliance with frameworks such as GDPR, HIPAA, and PCI-DSS.
Global cybercrime losses are projected to top US$10.5 trillion in 2025, highlighting the scale of the threat. Meanwhile, the Verizon 2025 Data Breach Investigations Report shows phishing and credential-based attacks remain dominant, with roughly 15% of all breaches beginning with phishing.
According to RFC 7489 of the IETF, DMARC has the unique ability to allow email senders to set preferences for authentication. By enabling it, you can also get reports on email handling and potential domain abuse. This makes DMARC stand out in terms of domain validation.
As per our latest DMARC statistics, a significant number of domains are still vulnerable to phishing attacks due to a lack of DMARC implementation.
To start the setup process for DMARC, a proper DNS changes and include DNS TXT records for the protocols. However, manual implementation of the DMARC protocol can be quite complex for non-technical users. It may even get quite costly if you hire an external fractional CISO to manage it for your business. That’s why using a solution like PowerDMARC’s DMARC analyzer makes sense: it automates setup, streamlines your configuration, and saves both time and money. Let us guide you through the setup and help protect your brand today.
DMARC reporting options
Reporting options for DMARC include:
- Aggregate reports (rua=): Sent daily and provide high-level summaries of your email authentication results, including which IPs are sending mail on your behalf and how many messages passed or failed.
- Forensic reports (ruf=): Sent in real time and contain more detailed failure information for individual messages that did not authenticate.
These parameters enable organizations to gather valuable insights on DMARC authentication results, giving insight into the number of emails that fail or pass DMARC authentication. A DMARC report also helps:
- Identify potential issues and patterns of abuse
- Detect misconfigurations in their email setup
- Gain insights into email behavior and mail flows
- Review authentication results for SPF and DKIM protocols
Common Benefits and Challenges
DMARC offers strong protection and valuable visibility, but implementing it correctly also comes with operational and technical considerations. Understanding both the benefits and challenges helps set realistic expectations for deployment.
Benefits
- Domain spoofing prevention and phishing protection: Blocks unauthorized senders and reduces the risk of impersonation attacks.
- Email deliverability improvement (10–15%): Authenticated domains are trusted more by inbox providers, improving inbox placement.
- Visibility through reporting on sending sources: DMARC reports reveal who is sending mail on your behalf and how messages authenticate.
- Compliance with GDPR, HIPAA, and Google/Yahoo 2024 mandates: Helps meet security and authentication requirements set by regulators and major mailbox providers.
Challenges
- Implementation timeline (3–6 months for safe deployment): Moving from monitoring to full enforcement takes time and careful review.
- Discovery requirement for all legitimate email sources: Every sending system must be identified and authenticated before applying strict policies.
- Technical knowledge needs (DNS, SPF, DKIM): Proper setup requires familiarity with email authentication and DNS management.
- Third-party service authentication limitations: Some tools or platforms have restricted SPF/DKIM support, making configuration more complex.
Troubleshoot DMARC Policy Errors
When using DMARC, you may encounter an error message. The following are some common DMARC policy errors:
- Syntax errors: You should be wary of any syntax errors while setting up your record to make sure that your protocol functions correctly.
- Configuration errors: Errors while configuring the DMARC policy are common and can be avoided by using a DMARC checker tool.
- DMARC sp Policy: If you configure a DMARC reject policy, but set up your subdomain policies to none, you will not be able to achieve compliance. This is due to a policy override on your outbound emails.
- “DMARC Policy Not Enabled” error: If your domain reports highlight this error, it points to a missing DMARC domain policy in your DNS or one that is set to “none”. Edit your record to incorporate p=reject/quarantine and this should fix the problem.
DMARC Policy Enforcement with PowerDMARC
DMARC remains one of the most effective ways to protect your domain from spoofing, phishing, and unauthorized email use. By choosing the right policy mode (none, quarantine, or reject), you control how receiving servers handle suspicious messages and how strongly your domain is protected. Additional parameters like pct= and sp= help fine-tune your deployment, while reporting options such as rua and ruf give you clear visibility into authentication results, sending sources, misconfigurations, and potential abuse.
Although DMARC setup can be complex, especially when working across multiple third-party services or managing a full enforcement timeline, the long-term benefits are substantial: better deliverability, improved compliance, and stronger brand protection.
PowerDMARC’s DMARC analyzer makes this process simpler by automating configuration, streamlining policy management, and turning raw XML reports into actionable insights. If you want an easier, safer path to DMARC enforcement, our platform is designed to support you at every step.
Contact us today to implement a DMARC policy and monitor your results easily!
Frequently Asked Questions (FAQs)
What is the default DMARC policy?
You can check DMARC compliance by reviewing your DMARC reports and confirming that your emails pass SPF and DKIM alignment. If you’re using a platform with a reporting dashboard, like PowerDMARC, you can view your domain’s authentication status and see whether your messages meet DMARC requirements.
Which DMARC policy is best?
The best policy for maximum security is p=reject, as it blocks all unauthorized email.
However, the best strategy is to implement it in phases:
- Start with p=none to monitor reports without affecting deliverability.
- Move to p=quarantine to send failing emails to spam.
- Finish with p=reject only when you’re ready (i.e., only when you are confident all your legitimate emails are correctly configured).
How do I fix my DMARC policy?
You can manually fix your policy by entering your DNS management. Once in, you need to edit your DMARC TXT record. A more simple solution is to use our hosted solution to make changes to your policy with a single click.
Which DMARC policy would you use not to accept an email if the message fails the DMARC check?
To reject an email that fails the DMARC check, you would use the p=reject policy.
This policy explicitly instructs receiving email servers to outright block and completely refuse delivery of any message that fails DMARC authentication. The email will not appear in the recipient’s inbox or even their spam folder. If you’d still like to send the email to the spam or junk folder, you can use p=quarantine.
- SPF Permerror: What It Means and How to Fix It - December 24, 2025
- What Is DMARC? How It Works, Policies & Configuration Tips - November 28, 2025
- What Is a DMARC Policy? None, Quarantine, and Reject - November 27, 2025