Email authentication has become a significant practice in cybersecurity. This is the result of a rise in the impersonation of real and well-known organizations. According to Forbes, the cost associated with cybercrime is projected to reach $10.5 trillion annually by 2025.
This is why the adoption of email authentication protocols like DMARC becomes crucial. Domain-based Message Authentication, Reporting, and Conformance, or DMARC, can be placed in an email sender’s Doman Name System (DNS) as a text record. DMARC starts validating and securing emails once enabled. A DMARC policy has the power to prevent phishing, email spoofing, and ransomware attacks, and improve email delivery rates.
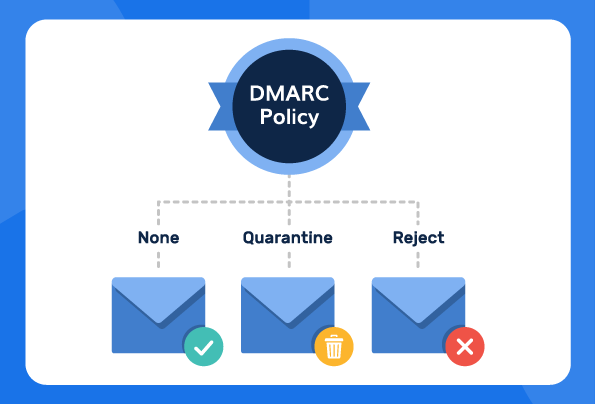
Your DMARC policy instructs email receivers how to handle messages that fail authentication. This policy can specify three possible actions:
- DMARC none
- DMARC quarantine
- DMARC reject
DMARC policy at “reject” can minimize the risk of domain abuse, brand impersonation, phishing, and spoofing attacks.
Securing Emails with DMARC
Emails can be easily forged, making it hard to tell the real deal from a dangerous fake. That’s where DMARC comes in. DMARC is like an email security checkpoint that verifies the sender’s identity before letting messages through. In fact, Verizon reports that more than 30% of all data compromises are a result of phishing attacks, highlighting the need for powerful protection like DMARC. By using DMARC, you can block spoofing attempts and ensure your inbox stays safe from fraudulent emails.
According to RFC 7489 of the IETF, DMARC has the unique ability to allow email senders to set preferences for authentication. By enabling it, you can also get reports on email handling and potential domain abuse. This makes DMARC really stand out in terms of domain validation.
To start the setup process for DMARC, you need to make a few DNS changes and include DNS TXT records for the protocols. However, manual implementation of this protocol can be quite complex for non-technical users. It may even get quite costly if you hire an external CISO to manage it for your business. PowerDMARC’s DMARC analyzer is therefore an easy alternative. We automate your DMARC policy setup, saving you both time and money.
I found PowerDMARC after the Google and Yahoo new email sender requirements were issued. PowerDMARC hooked us up with a monitoring DMARC policy in no time! It helped us slowly (but surely) shift to an enforced policy for better protection.”, reported small business owner Rachel R.
What is a DMARC Policy?
A DMARC policy is a set of DNS-level instructions that can be set up as a special TXT record. It tells receiving mail servers how to handle emails that fail authentication. It is denoted by the “p” tag in the DMARC record that specifies the action mail servers should take if an email fails DMARC validation.
A DMARC policy in practice can help you determine how strictly you want to handle emails that might try to impersonate your brand. Consider it a security guard for your domain. Depending on your ID, the guard determines whether he lets you into the building (in this case, your receiver’s inbox). He may prevent you from stepping in (reject), he may send you to a special place for further review (quarantine), or he may just let you in (none).
Your DMARC policy when at p=reject can help you prevent spoofing, phishing, and domain name abuse, acting like a “no-trespassing” sign for bad actors trying to impersonate your brand.
3 Types of DMARC Policies: p=reject, p=none, p=quarantine
Depending on the level of enforcement email domain owners want to establish, there are 3 primary DMARC policy types – none, quarantine, and reject. The main difference between these policy options is determined by the action taken by the receiving mail transfer agent when adhering to the specified policy defined by the mail sender in their DNS record.
Given below is a brief overview of the 3 DMARC policy types, along with detailed explanations:
- DMARC None: A “monitoring only” policy that serves no protection – good for the beginning stages of your deployment journey.
- DMARC Quarantine: Flags or quarantines unauthorized emails.
- DMARC reject: Blocks inbox access to unauthorized emails
1. DMARC None Policy
DMARC policy none (p=none) is a relaxed mode that triggers no action on the receiver’s side. This policy can be used to monitor email activity. It doesn’t provide any level of protection against cyberattacks.
None Policy Implementation Use Cases
Example: v=DMARC1; p=none; rua= mailto:(email address);
- The main aim of domain owners who select the “none” policy should be to gather information on sending sources and keep a tab on their communications and deliverability without any inclination towards strict authentication. This may be because they are not yet prepared to commit to enforcement, and are taking their time to analyze the current situation.
- Receiving email systems treat messages sent from domains configured with this policy as “no-action”, meaning that even if these messages fail DMARC, no action will be taken to discard or quarantine them. These messages will successfully reach your clients.
- DMARC reports are still generated when you have “p=none” set up. The recipient’s MTA sends aggregate reports to the domain owner, providing detailed email authentication status information for the messages that appear to originate from their domain.
2. DMARC Quarantine Policy
p=quarantine provides some level of protection as the domain owner can prompt the receiver to roll back emails into the spam folder to review later in case DMARC fails.
Quarantine Policy Implementation Use Cases
Example: v=DMARC1; p=quarantine; rua=mailto:(email address);
- Rather than outright discarding unauthenticated emails, the “quarantine” policy offers the ability for domain owners to maintain security while also providing the option to review emails before accepting them, taking the “verify then trust” approach.
- Changing your DMARC policy to DMARC quarantine ensures that legitimate messages that fail DMARC authentication will not be lost before you closely inspect them.
- This approach can be considered intermediate in terms of enforcement and facilitates a smooth transition to p=reject, wherein domain owners can a) assess the impact of DMARC on your email messages and b) make informed decisions regarding whether or not they should discard the flagged emails.
- The quarantine policy also helps reduce inbox clutter, ensuring your inbox doesn’t get overloaded with spam messages.
3. DMARC Reject Policy
Finally, the reject DMARC policy (p=reject) is an enforcement policy. It ensures messages failing authentication for DMARC are rejected. DMARC reject provides maximum enforcement by discarding emails not authorized by you.
Reject Policy Implementation Use Cases
Example: v=DMARC1; p=reject; rua= mailto:(email address);
- DMARC reject enhances your email security. It can prevent attackers from launching phishing attacks or direct domain spoofing. DMARC reject policy stops fraudulent emails by blocking out messages that appear suspicious.
- If you are confident enough not to quarantine suspicious messages, the “reject” policy is suitable for you.
- It is important to thoroughly test and plan before opting for DMARC reject.
- Make sure reporting is enabled for your domain when on DMARC reject.
- To DIY your enforcement journey, start at p=none and then slowly move to reject while monitoring your daily reports.
- Ideally, opt for our hosted DMARC solution to get expert assistance. Our professionals guide your DMARC implementation and throughout your enforcement journey.
Benefits of Enforcing Your DMARC Policy
Let’s delve into the advantages of setting up a strict DMARC policy for your domain:
1. Direct Protection Against Phishing and BEC
At DMARC reject (at DMARC enforcement), emails originating from unauthenticated sources are discarded. This prevents fraudulent emails from reaching your recipient’s inbox. It therefore offers direct protection against phishing attacks, spoofing, BEC, and CEO fraud.
This is especially important because:
- Verizon’s 2023 data breach investigation report found that 36% of all data breaches involve phishing
- Fortra’s 2023 BEC report concluded that cybercriminals love impersonating well-known brands
2. The First Line of Defense Against Malicious Software
Ransomware and Malware are often spread via fake emails sent from impersonated domain names. They can infiltrate and completely take over your operating system. A DMARC policy at reject ensures that unauthenticated emails are blocked out of your client’s inbox. This automatically prevents your clients from clicking on harmful attachments. And further minimizes the chances of unknowingly downloading ransomware or malware into their system. Here, your DMARC policy acts as an elementary line of defense against these attacks.
3. To Monitor Your Email Channels
If you simply want to monitor your message transactions and sending sources, a DMARC at p=none is enough. This will, however, not protect you against cyberattacks.
4. To Review Suspicious Emails Before Delivery
If you don’t want to block unauthorized emails outright, you can quarantine them. Simply leverage the quarantine DMARC policy to review suspicious messages before accepting them. This will lodge emails in your quarantine folder instead of your inbox.
Which is the Best DMARC Policy Type and Why?
DMARC reject is the best DMARC policy if you want to maximize your email security efforts and enable Gmail’s blue tick feature. This is because when on p=reject, domain owners actively block unauthorized messages from their clients’ inboxes. Your DMARC policy provides a high degree of protection against cyberattacks. This includes direct-domain spoofing, phishing, and other forms of impersonation threats. Hence, it also doubles up as an effective anti-phishing policy.
At DMARC enforcement, you can also implement BIMI. BIMI lets you enable blue checkmarks for your emails in Gmail and Yahoo inboxes – which is quite cool!
Busting Common DMARC Policy Myths
There are some common misconceptions about DMARC policies. Some of these can have terrible consequences on your mail delivery. Let’s learn what they are and what the truth is behind them:
1. DMARC None Can Prevent Spoofing
DMARC none is a “no-action” policy and cannot protect your domain against cyberattacks. Attackers often exploit the p=none policy to impersonate domains.
Over the years, several domain owners have reached out to PowerDMARC, explaining how they are being spoofed even with DMARC implemented. On further review, our experts found out that most of them had their DMARC policy configured at “none”.
2. You Won’t Receive DMARC Reports at p=none
Even when on p=none you can continue to receive daily DMARC reports by simply specifying a valid email address for the sender.
3. DMARC “Quarantine” is Not Important
Often overlooked, the quarantine policy in DMARC is extremely useful for your transitional phases. Domain owners can deploy this to make a smooth transition from no-action to maximum enforcement.
4. DMARC Reject Impacts Deliverability
Even on DMARC reject, you can ensure your legitimate emails are delivered seamlessly. Monitoring and analyzing the activities of your senders can help. You must also review your authentication results to detect failures faster.
Troubleshoot DMARC Policy Errors
The following are some common DMARC policy errors you may encounter:
Syntax Errors
You should be wary of any syntax errors while setting up your record to make sure that your protocol functions correctly.
Configuration Errors
Errors while configuring the DMARC policy are common and can be avoided by using a DMARC checker tool.
DMARC sp Policy
If you configure a DMARC reject policy, but set up your subdomain policies to none, you will not be able to achieve compliance. This is due to a policy override on your outbound emails.
“DMARC Policy Not Enabled” Error
If you come across this error message in your reports, this points to a missing DMARC domain policy in your DNS or one that is set to “none”. Edit your record to incorporate p=reject/quarantine and this should fix the problem.
A Safer Way to Update, Enforce, and Optimize Your DMARC Policy
PowerDMARC’s DMARC analyzer platform helps you effortlessly set up the DMARC protocol. Use our cloud-native interface to monitor and optimize your records with a few clicks of a button. Let’s explore its key benefits:
- PowerDMARC offers 7 views and filtering mechanisms for your DMARC Aggregate reports. Each view is designed to effectively monitor your email flows while in any DMARC policy mode.
- Aggregate reports are easy to read, human-friendly, and exportable
- Forensic reports can be encrypted to hide private information
- Our hosted DMARC feature allows you to update your DMARC policy modes easily. You can shift to p=reject and monitor your protocol effectively and in real-time. You won’t need to enter your DNS management console for this.
- Our 24-hour active support team will help you transition smoothly from a relaxed to an enforced DMARC policy. This can maximize your security while ensuring deliverability.
- You can set up custom email alerts to detect any malicious activity and take action against threats sooner
- We support multi-tenancy and multiple language translations on the platform. This includes English, French, German, Japanese, Dutch, Italian, Spanish, Russian, Norwegian, Swedish, and Simplified Chinese
Contact us today to implement a DMARC policy and monitor your results easily!
DMARC Policy FAQs
How do I know if my email is DMARC compliant?
PowerDMARC customers can easily assess their compliance by checking the dashboard summary. They can also analyze their current security posture with the help of PowerAnalyzer.
How do I fix my DMARC policy?
You can manually fix your policy by entering your DNS management. Once in, you need to edit your DMARC TXT record. A more simple solution is to use our hosted solution to make changes to your policy with a single click.
What is the default DMARC policy?
If you use our DMARC generator tool to add your policy, we assign “none” as the default mode. During manual implementation, you have to define your policy in the “p=” field. Otherwise, your record will be considered invalid.
Our Content and Fact-Checking Review Process
This piece of content was authored by a cybersecurity expert. It has been meticulously reviewed by our in-house security team to ensure technical accuracy and relevance. All facts have been verified against official IETF documentation. References to reports and statistics that support the information are also mentioned.
- Fix SPF Permerror: Overcome SPF Too Many DNS Lookups Limit - April 26, 2024
- How to Publish a DMARC Record in 3 Steps? - April 2, 2024
- Why is DMARC failing? Fix DMARC Failure in 2024 - April 2, 2024