Key Takeaways
- APTs are typically orchestrated by well-funded, highly skilled threat actors, often linked to nation-states or organized cybercrime groups, with the goal of stealing sensitive data, surveilling communications, or sabotaging systems.
- APTs follow a multi-stage cycle that encompasses reconnaissance, entry, persistence, movement, and data theft.
- Protection against APTs requires layered security: monitoring, regular updates, employee training, and threat response plans.
Cybercriminals continue to develop sophisticated attack tools, even as enterprise security technologies, like antivirus software and firewalls, advance in detecting and stopping threats. Many cybersecurity strategies still rely on the assumption that attackers choose their targets at random.
If a network has strong enough defenses, the logic goes, the attacker will simply move on to an easier target. However, this assumption no longer holds up in the face of advanced persistent threats (APTs).
Unlike opportunistic attacks, APTs are highly targeted. They select specific victims and continue their efforts relentlessly, regardless of the strength of the network’s defenses, until they succeed.
What Is an Advanced Persistent Threat?
An advanced persistent threat is essentially a prolonged and targeted cyberattack in which an intruder secretly infiltrates a network and stays hidden for an extended period of time. These types of threats are typically orchestrated by well-funded, highly skilled threat actors, often linked to nation-states or organized cybercrime groups, with the goal of stealing sensitive data, surveilling communications, or sabotaging systems.
Unlike ordinary cyberattacks that generally strike opportunistically and move on, an APT is calculated and targeted to infiltrate. To understand the full weight of the term, it helps to break down what each word actually means in this context:
- Advanced refers to the use of sophisticated hacking techniques and tools. These include custom malware, zero-day exploits, social engineering, and stealthy infiltration methods. APT actors often have access to significant resources and invest heavily in research and development, allowing them to evade standard security measures.
- Persistent describes the attacker’s commitment to maintaining long-term access and achieving their objective. Unlike opportunistic hackers who move on if their initial efforts are blocked, APT actors adapt and retry using various approaches until they successfully compromise the target. This persistence is methodical and strategic rather than random or hasty.
- Threat highlights the potential severity of damage. APTs are not minor annoyances; they pose serious risks to the confidentiality and integrity of critical systems and data. The consequences may include data theft, economic disruption, intellectual property loss, or even national security breaches.
How Advanced Persistent Threats Work
APTs operate methodically, following a multi-stage lifecycle that enables attackers to quietly bypass defenses and then remain inside a system for extended periods in order to extract maximum value from the breach. The whole process encompasses the following stages:
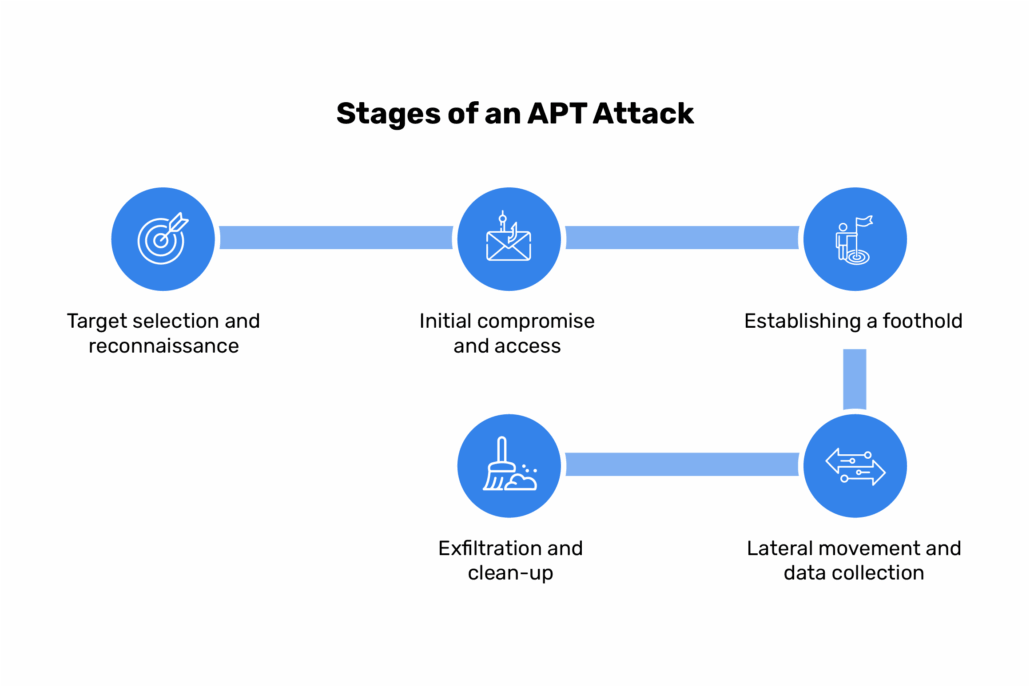
Target selection and reconnaissance
Target selection and reconnaissance is the first stage when attackers decide who to go after and why. Targets are often chosen based on the value of their intellectual property, sensitive data, or influence within critical sectors like defense, finance, or healthcare.
Once a target is selected, the attackers begin reconnaissance, gathering as much information as possible to increase their chances of success. This can include scanning for open ports, identifying vulnerable systems, analyzing employee email addresses, or even mining social media for behavioral insights. The more detail they gather, the easier it becomes to engineer a successful intrusion later.
Initial compromise and access
This stage deals with the point of entry. Even highly secured networks are vulnerable to human error and unpatched software, which attackers actively exploit.
Phishing emails (one of the most common options that attackers use to infiltrate systems) trick users into clicking malicious links or downloading malware-laced attachments. Other tactics include exploiting known software vulnerabilities or launching watering hole attacks that infect websites frequently visited by the target.
Once inside, the attacker’s first priority is to remain undetected. Techniques such as code obfuscation, fileless malware, and leveraging legitimate administrative tools help them blend into normal activity while avoiding security alerts.
Establishing a foothold
After gaining access, attackers aim to secure long-term access to the network. This is often achieved by installing backdoors or remote access trojans (RATs) that can reconnect even if the initial method of entry is closed off. Some attackers may create new user accounts or escalate privileges within the system to ensure they can move freely.
Maintaining persistence is crucial. Therefore, the attackers frequently test the network’s response patterns and adapt their tactics in order to avoid triggering alarms. At this stage, they often lurk for weeks or months, quietly observing and preparing for the next phase.
Lateral movement and data collection
Once a stable presence is achieved, attackers proceed with lateral movement and data collection. They begin exploring the network, seeking out valuable data and systems of interest.
Instead of attacking everything at once, APTs move strategically, hopping from one system to another, often using legitimate credentials they’ve harvested along the way. This makes their movements harder to detect.
During this phase, attackers map the internal environment, access file servers, databases, or communication platforms, and gather whatever information matches their goal, such as classified documents, trade secrets, financial records, or other credentials that provide access to external systems.
Exfiltration and clean-up
Data exfiltration is often done in small packets to avoid detection, sometimes disguised as normal web traffic or routed through encrypted tunnels. In more advanced cases, the attackers may compress and encrypt data before exfiltrating it, further masking their activity.
Once that is done, the attackers may either erase traces of their presence or deliberately leave hidden backdoors behind for future access. Clean-up operations can include deleting or modifying system logs, altering timestamps, or mimicking normal system activity to confuse forensic investigators.
Notable APT Examples
Over the past decades, APTs have left a lasting mark on cybersecurity history. While there have been many campaigns across different regions and sectors, the following examples stand out for their impact and geopolitical implications.
Stuxnet
Discovered in 2010, Stuxnet is often considered the first cyberweapon to cause real-world physical damage. It specifically targeted Iran’s nuclear enrichment facilities by infecting SCADA systems used to control centrifuges.
What made Stuxnet so groundbreaking was the technical precision of the malware as well as the political and strategic implications. This example demonstrated that state-sponsored cyberattacks could quietly breach highly secure infrastructure and sabotage industrial processes without firing a single shot.
Although no official government has publicly acknowledged responsibility, Stuxnet is widely believed to have been developed by the U.S. and Israel. The worm operated undetected for a significant period, highlighting the stealth and persistence typical of APT campaigns.
APT28 (Fancy Bear)
APT28 is a Russian-linked threat actor believed to be connected to the GRU, Russia’s military intelligence agency. This group has been active since at least the mid-2000s and is known for its politically motivated espionage.
APT28 has targeted government entities, military organizations, media outlets, and think tanks, especially in Europe and North America. One of its most high-profile operations was the cyberattack on the Democratic National Committee (DNC) during the 2016 U.S. presidential election.
The group is known for its use of spear phishing, malware distribution, and social engineering tactics, and it tends to focus on collecting information that supports Russian state interests.
APT29 (Cozy Bear)
Another Russian state-sponsored group, APT29, or as it is often referred to as Cozy Bear, is believed to be associated with Russia’s Foreign Intelligence Service (SVR). Unlike APT28’s aggressive and sometimes noisy tactics, APT29 is known for being stealthier and more patient.
Cozy Bear focuses on intelligence gathering and often maintains long-term access to its targets without detection. This group has been linked to cyber-espionage campaigns against Western governments, political organizations, and research institutions.
In recent years, the group drew international attention for attempting to steal COVID-19 vaccine research data. This was just another case that reinforced its reputation for targeting high-value, sensitive information tied to geopolitical interests.
How to Detect and Prevent APTs
According to Trellix’s CyberThreat Report, threat detection volumes linked to APT activity rose by 45% globally between Q4 2024 and Q1 2025. As APT actors become more active and their attack chains more complex, the need for proactive detection and layered defense becomes more urgent.
Organizations must adopt an approach that combines advanced technology with regular system maintenance and a well-prepared workforce in order to fight against persistent threats. To do so, they should work on the following areas of their cybersecurity.
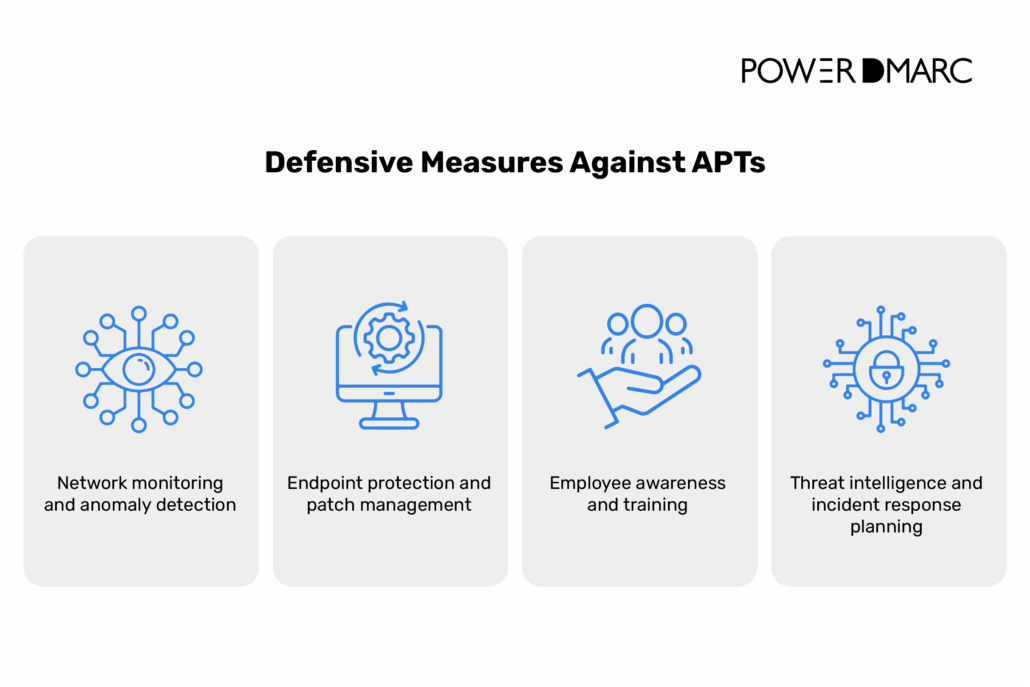
Network monitoring and anomaly detection
Detecting APTs starts with constant visibility into what’s happening across the network. Since APTs operate quietly, they often bypass obvious warning signs and blend in with normal network activity. That’s why constant, thorough monitoring is necessary for spotting known threats and for flagging unusual behaviors that deviate from baseline activity.
Behavioral analytics tools can help detect anomalies, such as unexpected data transfers, access attempts from unusual locations, or compromised credentials being used at odd hours. These subtle patterns may be the first clues that an APT has gained a foothold.
Endpoint protection and patch management
Workstations, servers, mobile devices, and other endpoints are often used as an entry point for APTs. Therefore, using protection platforms that detect suspicious activity and prevent malicious code execution can help prevent attacks.
Equally important is patch management since many APT groups exploit unpatched vulnerabilities to slip into systems unnoticed. Applying software updates quickly and automating patch deployment where possible helps close security gaps before attackers can exploit them.
Employee awareness and training
As mentioned, many APTs begin with phishing messages. Therefore, employees themselves are often the first line of defense.
A well-informed team can prevent attackers from ever getting a foot in the door. Phishing simulations and regular cybersecurity training are effective tools for building this awareness.
Employees should know how to spot suspicious emails, avoid unsafe links, use strong passwords, and report strange behavior immediately. These practices may seem small, but they make a significant difference in detecting and preventing APTs.
Threat intelligence and incident response planning
Fighting back always requires knowing your enemy. In the context of APTs, threat intelligence feeds are useful as they provide real-time insights into known attack methods, malicious IPs, and domain infrastructure linked to threat actors. This intel can inform firewall rules, blocklists, and other preventive measures.
ut when prevention fails, as it often does with APTs, you need a solid incident response plan. Such a plan requires clear communication protocols, containment procedures, recovery plans, post-incident reviews, and most importantly, a team that’s trained, ready, and able to act fast.
The Bottom Line
Although any data breach is a concern, APTs definitely stand out for their complexity and long-term impact. The fact that they often go unnoticed until real damage is done is what demands a proactive, layered security approach.
As we’ve emphasized throughout, email is often the weak link. If your defenses there are fragile, the rest of your network is at risk. However, PowerDMARC can help you take control by enforcing email authentication protocols like DMARC, SPF, and DKIM.
Book a demo today to strengthen your email perimeter. Don’t wait for an APT to remind you that not all breaches are easy to notice right away.
Frequently Asked Questions (FAQs)
What are the main differences between APTs and malware?
An APT is a long-term, targeted attack that typically uses multiple methods to infiltrate and stay hidden in a system, whereas malware is a single tool in the form of malicious software used in these attacks or by itself to cause harm.
How long do APT attacks typically last?
APT attacks can go on for months or even years. They’re built to stay hidden, quietly collecting data or gaining deeper access over time.
- How do I fix “DMARC Policy Not Enabled” in 2025? - August 25, 2025
- What Is SPF Email Record? Function, Syntax, and Errors - August 22, 2025
- What Is Data Exfiltration? Detection and Prevention - August 7, 2025



