
How to View Email Headers in Outlook?
BlogTo view email header in outlook, double click on the email whose email header you want to see. Select “Actions” from the menu at the top of the window.

Display Name Spoofing: Definition, Technique, Detection, and Prevention
BlogIn display name spoofing, hackers make fraudulent emails look legitimate by using different email addresses but the same display names.
How to View DNS Records for a Domain?
Blog To view DNS records for a domain, you need to perform a lookup on your domain name system. This is an instant and easy process and here are the steps for it.
SPF Format : SPF Basic & Advanced Formats Explained
BlogSPF format includes IP addresses allowed to send emails with 3 primary elements; SPF Mechanism, SPF Qualifiers, and SPF Modifiers.
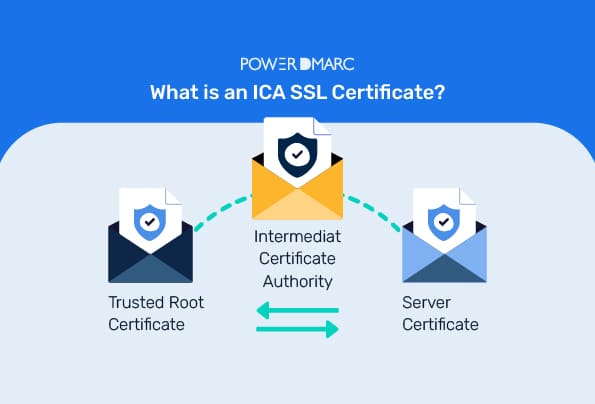
What is an ICA SSL Certificate?
BlogICA SSL certificates are digital certificates that help route your website’s SSL certificate to the root CA certificate, helping browsers and external web applications trust your online identity.

What is a DNS MX Record?
BlogA DNS MX record is a type of DNS record that stores the mail exchange server for a domain. It's used to route emails to the right place.
