What is BlackCat Ransomware? The FBI has recently issued a warning about a new strain of ransomware known as the BlackCat Ransomware (aka Noberus and AlphaV) that’s been wreaking havoc on businesses and personal computers across the globe (operating mainly in the US). FBI agents are concerned that BlackCat could become a serious problem for businesses if left unchecked. While most companies have strong security systems in place to keep out hackers, they may not be prepared for an attack like this one.
You can read the full article by Forbes, here.
BlackCat Ransomware: A new ransomware gang is on the loose
BlackCat uses similar encryption techniques as other types of ransomware, but also adds some additional security measures to make it more difficult to decrypt files if they are encrypted. This includes using two different encryption algorithms and making sure that the decryption key is never stored on the same drive as encrypted files.
The creators of BlackCat appear to be targeting businesses and organizations rather than individuals, which makes sense since these types of organizations tend to be more willing to pay the ransom than individuals would be.
BlackCat is a group of cybercriminals that targets businesses to steal their intellectual property and personal information. It’s known for targeting businesses in the construction and engineering, retail, transportation, commercial services, insurance, and machinery sectors.
The group also has attacked organizations in Europe and the Philippines. The largest number of its victims so far are from the U.S., but this could change as it continues to expand its reach across the globe.
D
What is BlackCat Ransomware: A Ransomware-as-a-Service (RaaS)
BlackCat Ransomware is a ransomware-as-a-service (RaaS) business model that relies on an affiliate marketing structure. Operating as a RaaS business model means that BlackCat does not host or distribute the malware itself—it relies on third parties to do so for them. Operating in this way allows BlackCat to avoid legal liability and also helps it avoid detection by antivirus software.
What is Ransomware-as-a-Service?
Ransomware-as-a-service (RaaS) is a relatively new type of cyberattack that allows anyone to purchase malicious software and use it to hold files hostage, usually, until a ransom is paid.
RaaS is extremely profitable for hackers because they can rent out their ransomware software to other criminals without having to worry about being caught by law enforcement, as they would if they were running their own attacks.
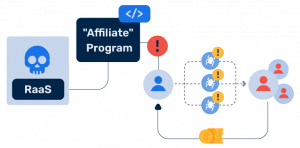
RaaS operates through the use of “affiliate” programs, which are essentially programs that allow people to earn money by spreading malware. Affiliates are paid for every victim they infect and for every time the malware generates revenue. The more successful an affiliate is at spreading RaaS, the more money they can earn.
How does it operate?
Ransomware is typically delivered via email or through a website that has been hacked. The malware then encrypts all of the user’s files and displays an alert stating that the user has violated federal laws, resulting in their computer being locked. The attacker then informs the user that they can unlock their computer by paying a ransom fee—usually between $200 and $600—via bitcoin or another cryptocurrency.
The reason RaaS criminals are able to get away with this type of scam is that most victims don’t report it when they’re infected with ransomware; instead, they try to fix the problem themselves by paying the ransom and hoping for the best.
Need protection against ransomware attacks? Read more about DMARC and Ransomware here.
The Anatomy of BlackCat Ransomware
Ransomware is considered a sophisticated infection method and has the potential to render an infected host unusable. It could cause major damage to an organization if not detected quickly. BlackCat ransomware has been downloaded via Microsoft Office files containing an embedded malicious executable. The payload contains code that allows the malware to spread across the compromised network, targeting both Windows and Linux systems.
The BlackCat ransomware is described as a “multi-stage” attack with the aim of exploiting Active Directory (AD) user and administrator accounts in order to encrypt files on targeted computers. In addition, BlackCat/ALPHV ransomware leverages previously compromised user credentials to gain initial access to the victim system.
How to prevent BlackCat Ransomware?
Manual steps to prevent BlackCat Ransomware attacks:
- Update your software regularly. Ransomware typically targets older systems or systems that haven’t been updated in a while, so make sure you know what software is running on your computer, and make sure it’s up-to-date.
- Back up all of your files regularly and store them in two different places (like on two different external hard drives). This way if one drive fails or gets infected with malware, you’ll still have copies of all your files somewhere else on another drive or in the cloud somewhere safe from harm!
- Use strong passwords that aren’t reused anywhere else (especially not multiple times across different accounts), and never click on links sent through email—even if they look like they come from someone you trust!
- Don’t pay the ransom! Paying criminals is just throwing money away. The only way they’ll unblock your data (they claim) is if you pay them first—but they’re lying! Don’t fall for it!
- Try using Windows’ built-in file recovery tool to restore your files from Shadow Copies (a backup system). It may not work 100% of the time but it’s definitely worth a shot! You can find this tool under “System Restore” in your Control Panel (search for “System Restore” if you don’t see it right away).
Tools you can deploy to prevent BlackCat Ransomware attacks:

1. The good news is that there’s an emerging technology that can help you protect your business from BlackCat ransomware: DMARC.
A DMARC policy allows email senders to tell receiving servers whether or not email messages are legitimate. This means that if an attacker tries sending a phishing email with malicious code attached, the recipient’s server will know that it’s not coming from the legitimate domain owner and can reject it before any damage is done.
Get your free DMARC analyzer today.
2. Multi-factor authentication (MFA) is a way to keep hackers out of your accounts while still letting you access them freely. By using two or more pieces of information to verify your identity, it’s much harder for someone who has stolen your password or other identifying information to get into your account without being detected by MFA.
3. Firewalls can protect against many BlackCat ransomware attacks. A firewall is software that works with your operating system to block unauthorized access to your computer, which includes access by malicious code like ransomware. Most operating systems include firewalls, but if you don’t have one or want an extra layer of protection, there are plenty of free options out there—and many are easy to install.
- DMARC MSP Case Study: CloudTech24 Simplies Domain Security Management for Clients with PowerDMARC - October 24, 2024
- The Security Risks Of Sending Sensitive Information Via Email - October 23, 2024
- 5 Types of Social Security Email Scams & How to Prevent Them - October 3, 2024




