CISOs and organizations strive to keep up with cybersecurity tools, techniques, and practices. However, threat actors continuously innovate to outsmart them. One such technique they use is the watering hole attack. When your technical ecosystem is secured and your employees are trained to avoid manipulation, cybercriminals may target third-party services. This is done to exploit vulnerabilities and cause harm to your organization.
Key Takeaways
- Watering hole attacks target users by compromising frequently visited websites to spread malware.
- The attack lifecycle includes stages such as website identification, target research, infection, luring, and exploitation.
- Regular updates for software and plugins are essential to mitigate vulnerabilities that could be exploited in watering hole attacks.
- Implementing network segmentation helps contain threats and limits the potential impact of an attack.
- Organizations should ditch legacy systems to reduce susceptibility to attacks and benefit from modern security features.
History of Watering Hole Attacks
The term “watering hole attack” originates from an ancient hunting strategy. Hunters in ancient times found it inconvenient to chase down prey. This is because, the prey was ideally faster, and much more agile than humans. A much better solution was laying traps where the prey were likely to gather. Places like a riverside or watering hole attracted these prey for drinking water.
Hunters would lie in wait at the watering hole for their prey’s guard to go down so they could easily pin them down. The same goes for this emerging cyberattack technique.
Protect Against Watering Hole Attacks with PowerDMARC!
Watering Hole Attack Definition
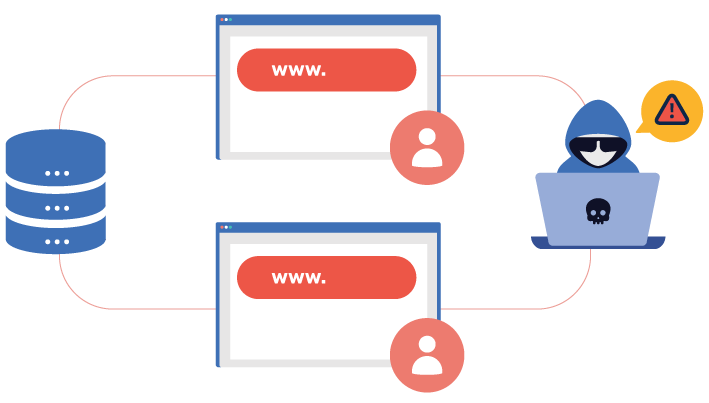
A watering hole attack is a cyberattack in which threat actors compromise end users by guessing or observing websites they frequently visit. The attackers aim to infect the websites with malware to infiltrate a target’s device. Then, they can use the infected device to gain access to the target’s organizational network.
For example, a hacker aims to exploit a company’s computer. But, its cybersecurity systems and employees’ cyber hygiene practices prevent them from infiltrating. However, the hacker knows that HR orders cake from a particular online bakery for every employee’s birthday. Now, they will wait for HR to visit the baker’s website. They will launch malware or executable codes onto the HR’s device. This will ultimately allow them to enter the company’s ecosystem.
Watering hole attacks are dangerous because they are difficult to spot and eliminate. By the time you figure out their presence, hackers will have done enough harm to your company.
Complete Lifecycle of a Watering Hole Attack
A typical watering hole attack unfolds in the following stages:
1. Website Identification
Threat actors often select their websites with security vulnerabilities, i.e. poor security practices. Their targets could be employees of a particular company, members of a specific industry, or users of a certain software or service. They consider several factors when locking an ideal target.
These include social engineering opportunities, geographical location, proximity to their setup, expected financial gains, reputation, vulnerabilities, and ease of exploitation.
2. Target Research
Next up, they research the target’s online behavior and patterns. This helps them find a watering hole (any third-party website they visit regularly). These can be news websites, industry forums, file format converters, online shopping platforms, ticket booking websites, etc.
3. Infection
The attackers compromise one or more of these websites by injecting malicious code into them. This code can trick visitors into downloading malware onto their computers or devices.
4. Luring
After malicious code is set in the ‘watering hole’ website, bad actors wait for their targets to visit the compromised website. Hence, the analogy to predators waiting at a watering hole for prey. The infected website is the lure or bait for victims to fall into the trap.
5. Exploitation
When the victim visits the ‘watering hole’ website, their computer gets infected with malware or compromised. This could happen through drive-by downloads. This is where the malware is auto-downloaded and executed without the user’s knowledge or consent.
6. Payload Delivery
The malware installed through the ‘watering hole’ website can include various payloads. This depends on the attacker’s goal. Gaining unauthorized access to their devices and networks may be a possible objective.
7. Covering Tracks
Once attackers have achieved their goals by exploiting the targeted system, they often try to cover their tracks. This involves removing traces of their presence by manipulating or deleting log files. They may alter timestamps, delete specific entries, or even tamper with log configurations to prevent logging altogether.
Hackers may even use stealthy techniques, such as rootkits, to hide their presence on compromised systems. Rootkits modify the operating system to conceal malicious processes and activities.
Real-Life Example of a Watering Hole Attack
In 2021, Google’s Threat Advisory Group (TAG) uncovered a series of watering hole attacks. These attacks targeted iOS and macOS devices. The attacks were primarily operating in Hong Kong. They compromised websites and a combination of vulnerabilities, including a zero-day exploit in macOS Catalina (CVE-2021-30869).
The watering hole points were websites linked to a media outlet and a pro-democracy group. The attackers installed a backdoor on vulnerable devices through the exploit chain. This provided them with a range of capabilities. These included device identification, audio recording, screen capturing, keylogging, file manipulation, and executing terminal commands with root privileges.
Protection Against Watering Hole Attacks
Preventing watering hole attacks involves a combination of cybersecurity measures and user awareness. Here’s what you, as the owner of an organization, can do-
-
Keep Your Software and Plugins Updated
Keeping software and plugins updated is crucial for maintaining security as updates often include patches for known vulnerabilities, protecting against exploits that could lead to unauthorized access, data breaches, or malware infections.
-
Implement Least Privilege
Follow the principle of least privilege by granting users only the permissions and access they need to perform their jobs. Limiting user privileges can mitigate the impact of successful watering hole attacks. This is because it reduces the attacker’s ability to escalate privileges and move laterally within the network.
-
Network Segmentation
Divide your network into smaller and isolated segments to limit the impact of a watering hole attack. This will allow you to control and contain the spread of malware. It also prevents attackers from accessing sensitive systems and data. Reducing the attack surface enables prioritization of network traffic based on business needs and criticality. This enhances performance, reduces congestion, and optimizes bandwidth usage.
-
Implement Web Filtering
Web filtering prevents watering hole attacks by blocking access to malicious websites. web filtering solutions can prevent unauthorized data exfiltration. Web filtering solutions can prevent unauthorized data exfiltration as well.
This is achieved by blocking outbound connections to known command and control servers used by malware. This helps contain the impact of watering hole attacks and prevent sensitive information from being stolen or leaked.
-
Ditch Legacy Systems
Ditching legacy systems protects organizations from watering hole attacks. This is done by eliminating outdated software and infrastructure vulnerable to exploitation.
Modern systems and software are equipped with built-in security features. These include advanced encryption protocols, secure coding practices, and threat detection capabilities. These features make it more difficult for attackers to compromise systems and networks.
Wrapping Up
The potential for lucrative rewards incentivizes cybercriminals to continue employing watering hole attacks. This includes gaining unauthorized access to valuable resources or obtaining sensitive data.
Ongoing monitoring for watering hole attacks allows you to deploy robust cybersecurity measures. This helps you stay ahead of emerging threats in the ever-evolving cyber landscape. In the end, this safeguards your brand’s reputation and maintains trust with customers.
If you wish to protect your domain against email fraud, you need our DMARC analyzer. Sign up for a free trial to experience the power of email authentication today!
- How to Prevent Spyware? - April 25, 2025
- How to Set Up SPF, DKIM, and DMARC for Customer.io - April 22, 2025
- What is QR Phishing? How to Detect and Prevent QR Code Scams - April 15, 2025




