PowerDMARC’s Email Authentication Blog – Read the latest news and updates
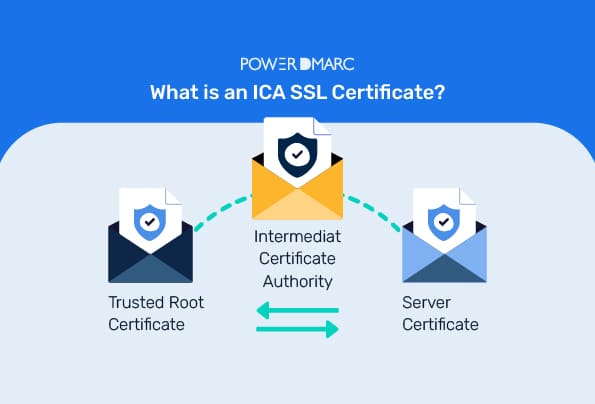
What is an ICA SSL Certificate?
BlogICA SSL certificates are digital certificates that help route your website’s SSL certificate to the root CA certificate, helping browsers and external web applications trust your online identity.

What is a DNS MX Record?
BlogA DNS MX record is a type of DNS record that stores the mail exchange server for a domain. It's used to route emails to the right place.

Apple BIMI Adoption and Support
BlogIn recent news, Apple BIMI adoption was announced in their new iOS update, pushing email service providers to further extend their adoption rate of the new email authentication + marketing tool that has become the talk of the town: Brand Indicators…

Spear Phishing VS Phishing
BlogSpear phishing is a targeted form of phishing that uses personal information to convince the recipient to take a specific action.

What are Romance Scams?
BlogIn Romance Scams, con artists use online dating sites to dupe victims into sending money and gifts.

What is Clone Phishing?
Blog Clone phishing imitates alert emails from reputable companies to trick consumers into disclosing private information like usernames and passwords.

What is Vishing?
BlogVishing is the act of tricking someone into disclosing their personal or financial information by calling them on their telephone.

What is Smishing?
BlogSmishing is a combination of SMS and phishing. A form of text message phishing, smishing may be used by cybercriminals to obtain your financial data or access your computer remotely.

What Is Business Email Compromise?
BlogBusiness Email Compromise (BEC) occurs when a hacker gains access to a company email account and assumes the account holder's identity to commit fraud against the company.

DMARC and Mailing Lists
BlogWhile your email authentication protocols may break with the use of mailing lists, there are ways to resolve this issue.
