
What is Information Security?
Blog Information security is the process of ensuring that information is kept safe from unauthorized access, use, or disclosure.

Best DDoS Attack Tools
BlogUsing DDOS attack tools can be very helpful in protecting your system or network. These tools are crucial for system admins and pen testers

What is Piggybacking?
Blog Piggybacking is a cybersecurity risk that can lead to unauthorized access exploiting legitimate users. Prevent it now!
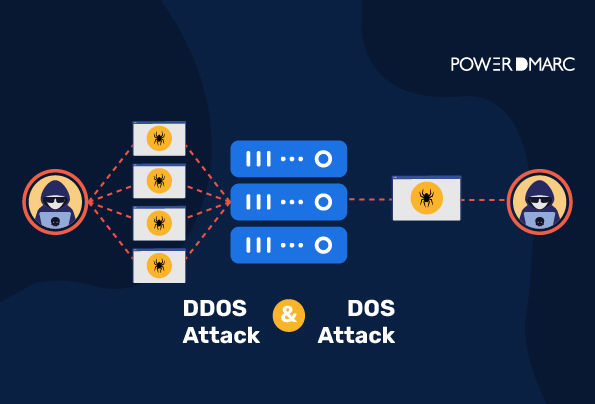
Understanding DoS and DDoS
BlogDoS vs DDoS: DoS and DDoS attacks are types of cybercrime that can defraud victims by rendering their systems, account, website or network resource unusable.

What is Ransomware?
BlogThe purpose of ransomware is to encrypt your important files using malicious software. The criminals then demand payment from you in exchange for the decryption key.
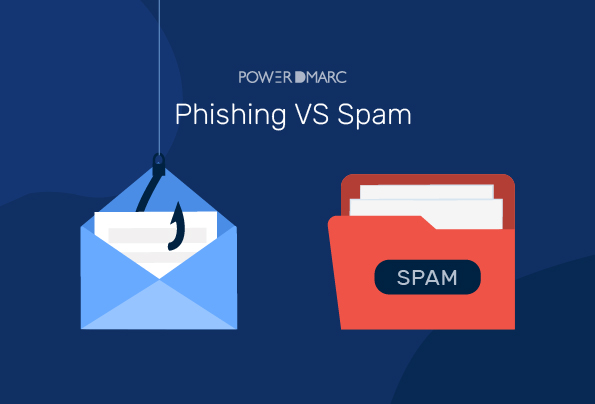
Phishing vs Spam
BlogPhishing and spam are both designed to trick you into taking action you wouldn't normally take, such as opening an attachment or clicking on a link.
