Microsoft 365 inbound emails failing DMARC did not get rejected, even with a DMARC policy set to “p=reject”. This was done to avoid blocking legitimate emails that may get lost during transmission due to email security policies on the sender’s side.
Key Takeaways
- Microsoft 365 does not reject DMARC fail emails to prevent blocking legitimate messages.
- Marking failed DMARC messages as spam allows users to receive potentially important emails.
- Creating a “safe sender” list can help ensure legitimate emails reach your inbox.
- Transport rules can be configured to quarantine or warn about unauthorized inbound emails.
- DMARC policies set to “p=reject” can lead to the loss of legitimate emails if not properly configured.
Why did Microsoft 365 not reject DMARC fail emails?
Microsoft 365 didn’t reject emails that fail the DMARC check in order to:
- Avoid false negatives that may result from email forwarding scenarios and the usage of mailing lists
- Avoid legitimate emails from being rejected due to configuration problems on the sender’s side
Due to this, Microsoft 365 email security deemed it better to mark messages as spam instead of outright rejecting them. Users can still leverage Microsoft to receive these emails in their inboxes by:
- Creating a “safe sender” list
- Creating a transport rule, also known as an Exchange Mail Flow Rule
While your legitimate emails failing DMARC may be worrisome, this tactic may result in malicious emails evading DMARC checks to make their way into users’ inboxes.
You can check out this document by Microsoft 365 for Inbound DMARC configuration in their Exchange Online platform
Simplify Security with PowerDMARC!
How to Create Microsoft 365 Transport Rule to Quarantine Unauthorized Inbound Emails?
To address these concerns regarding Office 365 DMARC deployment, we can create an Exchange Mail Flow/ Transport rule using the sender’s message header.
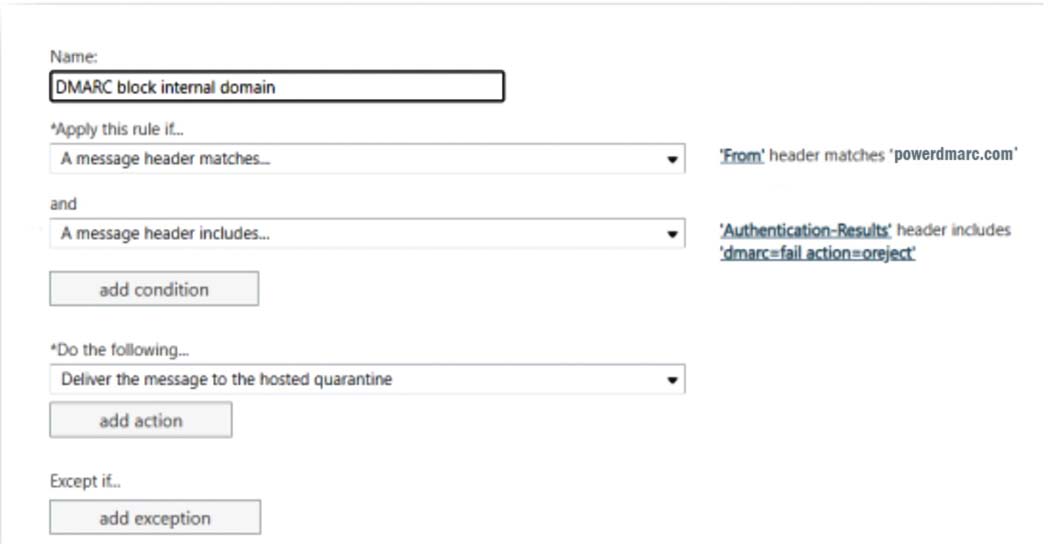
Case 1: Setting up Transport Rule to Quarantine Inbound Emails from Internal Domains
If mail is received by internal domains in the “From” address, we can set up a transport rule to quarantine the emails. This will lodge the email into the user’s quarantine folder instead of their inbox.
The rule verifies:
- Whether the From field matches your own domain
- Whether DMARC is failing for the message
This would determine what action needs to be taken.
Note: Before you configure this rule it is recommended that you deploy it on a restricted user base to test the soil before going for large-scale deployment. Make sure your authorized senders are passing DMARC, failing which would indicate misconfigurations and may lead to the loss of legitimate emails.
To set up the rule follow the steps below:
- Log in to your Exchange Online admin center
- Go to Mail flow > Rules
- Create a new rule by selecting the Add icon > Create a new rule
- Set “Match sender address in message” to “Header”
- In Apply this rule if…, you can select the condition you want to apply this rule to from the drop-down menu. Here we want to configure the rule if the DMARC authentication result is “fail” and if the “From” domain matches your own domain name
- In Do the following…, you can now select your action and set it to “Deliver the message to the hosted quarantine”
- Click Save
Case 2: Setting up Transport Rule to Quarantine Inbound Emails from External Domains
If you receive emails from domains that do not fall within the scope of your organization (external domains) that fail DMARC, you can set up a disclaimer that would warn users of a possible phishing attempt or malicious intent.
Note: Prepending a disclaimer for external domains failing DMARC can be beneficial if you don’t want to outright restrict emails. More often than not misconfigured protocols on the sender’s side may contribute to failed authentication checks.
To set up the rule follow the steps below:
- Log in to your Exchange Online admin center
- Go to Mail flow > Rules
- Create a new rule by selecting the Add icon > Create a new rule
- Set “Match sender address in message” to “Header”
- In Apply this rule if…, you can select the condition you want to apply this rule to from the drop-down menu. Here we want to configure the rule if the DMARC authentication result is “fail”.
- In Do the following…, you can now select your action and set it to “Prepend the disclaimer..” and add set your desired disclaimer

- You can now add an exception to this rule like in case the “From” header matches your domain name
- Click Save
How to Create Microsoft 365 Transport Rule to Reject Unauthorized Inbound Emails?
- Log in to your Exchange Online admin center
- Go to Mail flow > Rules
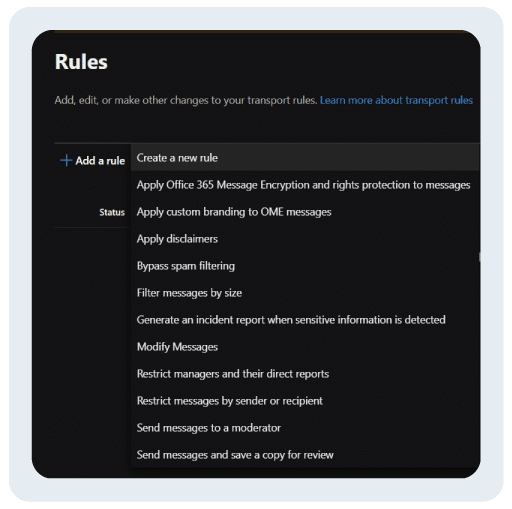
- Selecting + Add a rule
- Click on Create a new rule from the drop-down menu
- Name your mail flow rule. For example: DMARC Policy Override
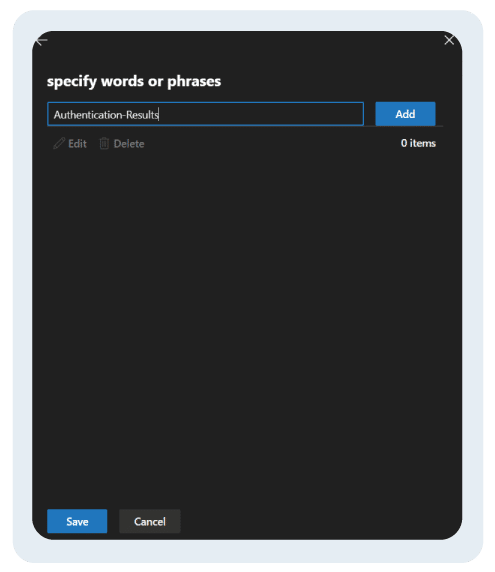
- Under “Apply this rule if” select “the message headers include any of these words”
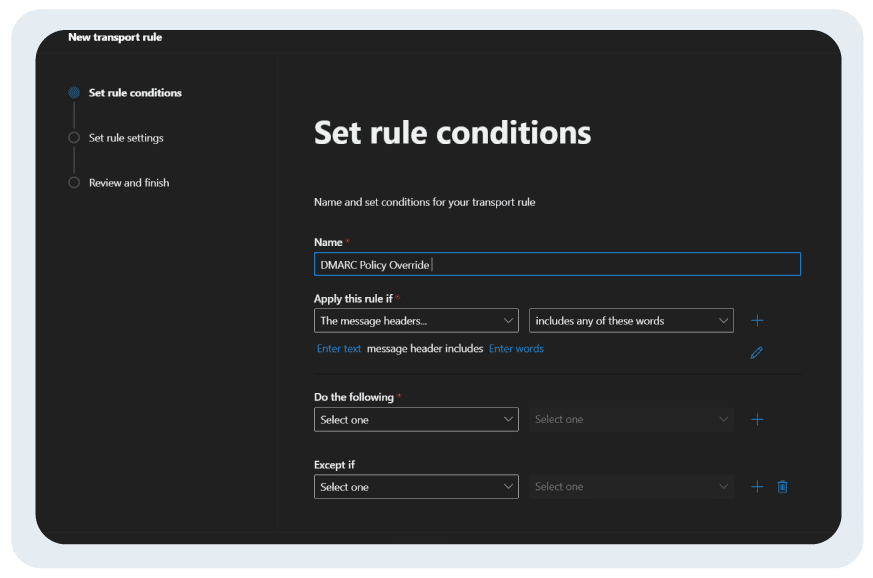
- Now click on “Enter text” in blue highlighted text and select “Authentication-results”
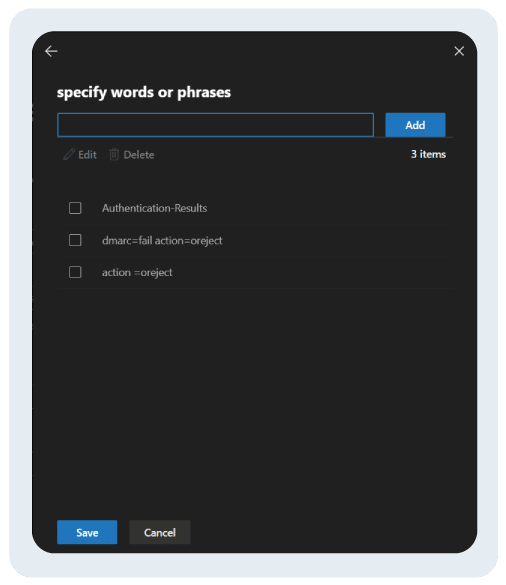
- Similarly. Click on “Enter words” in blue highlighted text and select the option of your choice or all options.
- Under “Do the following” select “Block the message”
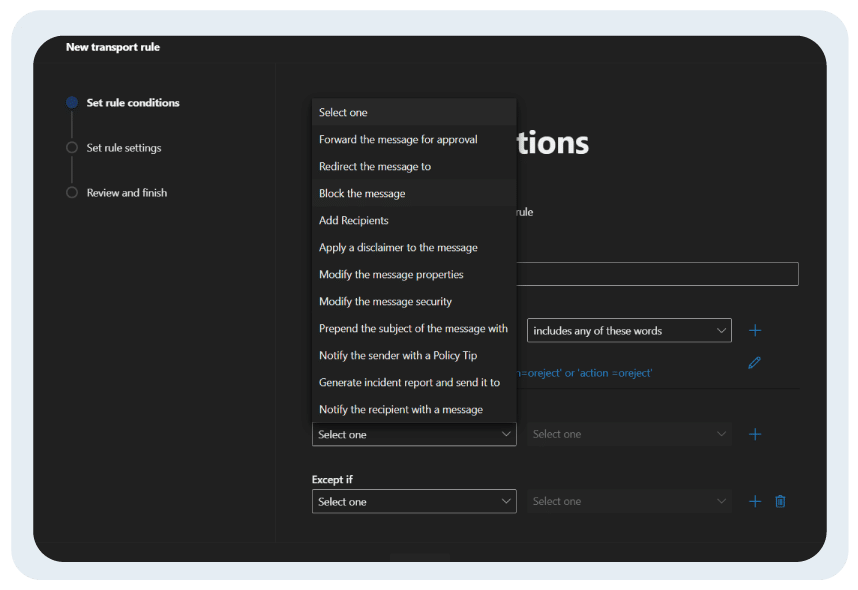
- Further choose “reject the message and include an explanation”
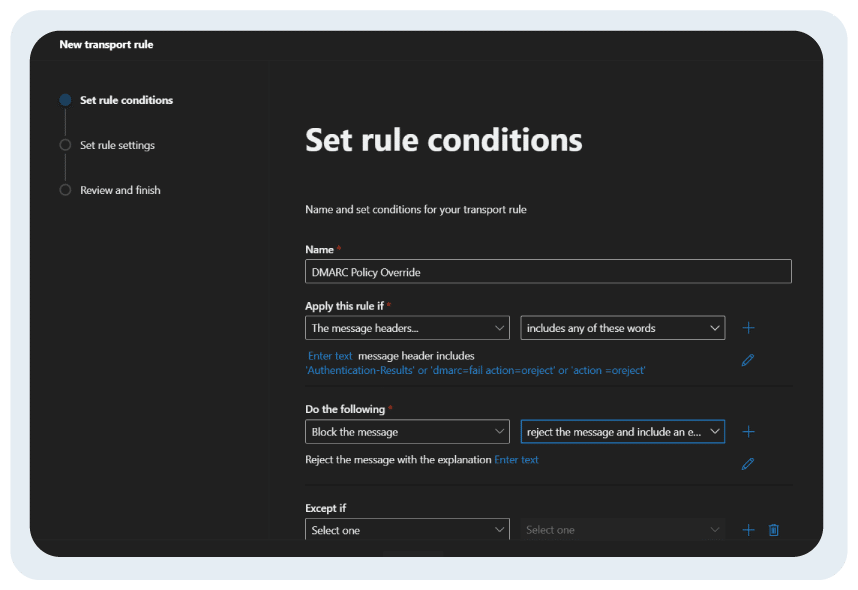
Save the mail flow rule. It may take a few minutes to process the changes, and you’re done!

Microsoft Announces New Policy Handling Approach: Updated June 20, 2023
In June 2023, Microsoft announced important changes to DMARC policy handling for consumer services (live.com / outlook.com / hotmail.com) :
- If a sender has configured an enforced DMARC policy or “reject” or “quarantine”, Microsoft will honor the sender’s policy by rejecting or quarantining emails that fail DMARC authentication, instead of delivering them.
- Once the action is taken, Microsoft will send a Non-Delivery Report (NDR) to the sender with an error message: “550 5.7.509: Access denied, sending domain example.com does not pass DMARC verification and has a DMARC policy of reject”.
Note: For enterprise customers, Microsoft 365 now honors the sender’s DMARC policy (e.g., p=reject, p=quarantine) by default by rejecting or quarantining messages that fail DMARC when your domain’s MX points directly to Office 365. You can customize this behavior per policy in the Microsoft 365 Defender portal under Anti-Phishing settings. If your MX points to a third-party security solution, DMARC enforcement may not apply unless Enhanced Filtering for Connectors is enabled.
DMARC Now Mandatory For Microsoft Bulk Senders
It’s important to note that DMARC is not optional for 5000+ email senders per day, per domain, to Microsoft consumer services. According to the new requirements:
- High-volume senders must implement SPF and DKIM with both passing for the sending domain
- High-volume senders must implement and pass DMARC, at at least p=none, aligned against either or both SPF and DKIM.
PowerDMARC helps meet these requirements quickly and safely for global enterprises, and businesses of all sizes! To get started, contact us today to speak to an expert.
Some Important Points to Remember
- DMARC doesn’t protect against spoofing lookalike domains and is only effective against direct-domain spoofing and phishing attacks
- A DMARC policy set to “none” would not quarantine or reject emails failing DMARC, only p=reject/quarantine can protect against spoofing
- DMARC reject is not to be taken lightly as it may lead to the loss of legitimate emails.
- For safer deployment, configure a DMARC reporting tool to monitor your email channels and authentication results on the daily