Key Takeaways
- SPF records are written using a defined syntax that includes mechanisms such as “include”, “a”, “mx”, and “ip4/ip6”. These mechanisms allow domain owners to specify trusted servers in a structured way.
- The exact SPF record you need depends on whether your organization uses its own mail servers, relies on third-party providers, or operates in a hybrid environment.
- Pairing SPF with DKIM and DMARC creates a multi-layered authentication strategy that strengthens your defense against phishing, spoofing, and domain abuse.
Email spoofing and phishing remain persistent threats for businesses worldwide, making email authentication more important than ever. If you’re asking “what SPF do I need,” you’re already taking a key step toward protecting your domain and safeguarding your brand’s reputation.
SPF (Sender Policy Framework) is a DNS TXT record that tells receiving mail servers which IP addresses and servers are authorized to send emails on behalf of your domain. Without proper SPF configuration, your legitimate emails may end up in spam folders, while cybercriminals can easily impersonate your domain.
Understanding what SPF you need requires evaluating your current email setup and ensuring all legitimate sending sources are properly authorized.
What Is SPF in Email?
SPF is an email authentication protocol implemented through a DNS TXT record. Its purpose is to specify which mail servers and IP addresses are authorized to send emails on behalf of your domain. By publishing this information, you create a reference point that receiving mail servers can check when deciding whether to accept a message.
SPF records are written using a defined syntax that includes mechanisms such as “include“, “a“, “mx“, and “ip4/ip6“. These mechanisms allow domain owners to specify trusted servers in a structured way. For instance, “include” brings in the SPF policies of third-party providers, while “mx” authorizes servers that handle your domain’s incoming mail. Together, these elements create a precise set of instructions for mail servers, ensuring that only legitimate senders are recognized.
Why Is SPF Important?
SPF authentication delivers multiple advantages that directly improve both security and email performance.
First, SPF helps prevent email spoofing and phishing attempts by making it significantly harder for cybercriminals to impersonate your domain in malicious emails. With this protection in place, attackers lose a key method of exploiting your brand identity in fraudulent campaigns.
SPF also enhances email deliverability. Internet service providers and platforms like Gmail, Outlook, and Yahoo use SPF validation as an important requirement when deciding whether to trust an incoming email. A properly configured SPF record signals to these services that your emails are legitimate, which increases the likelihood that your messages will land in inboxes rather than junk folders.
SPF protects your brand reputation by preventing unauthorized use of your domain in spam or phishing campaigns. When customers know that emails truly originate from you, confidence in your organization grows, and you maintain stronger control over your communication channels.
How SPF Works
The SPF authentication process operates through a clear, step-by-step verification sequence that takes place every time an email is sent. Having a thorough understanding of this process makes it easier to configure accurate SPF records that match the unique structure of your email environment.
The process begins when your organization publishes an SPF record in your domain’s DNS settings. This record acts like a public rulebook, specifying which IP addresses, mail servers, and third-party services are permitted to send emails on your behalf.
When someone sends an email claiming to come from your domain, the receiving mail server initiates an SPF lookup by checking your domain’s DNS records. It then compares the IP address of the sending server against the authorized sources listed in your SPF record.
If the sending server is included, the message passes SPF authentication, signaling to the recipient system that the email can be trusted. However, if the sending server is not listed as authorized, the email fails SPF. Depending on the policy you’ve configured, the receiving server may reject the email outright, quarantine it, or send it to the recipient’s spam folder. This entire sequence occurs automatically and within milliseconds, making SPF a highly efficient protective layer.
What SPF Record Do You Need?
Determining what SPF you need requires a careful review of your email infrastructure to identify every legitimate source that sends messages on your domain’s behalf. The exact SPF record you need depends on whether your organization uses its own mail servers, relies on third-party providers, or operates in a hybrid environment.
For organizations using their own mail servers, your SPF record needs to include your server’s IP addresses using “ip4” or “ip6” mechanisms. An example of this is:
- v=spf1 ip4:192.0.2.1 -all
This record authorizes a single IPv4 address to send emails for your domain, while the -all mechanism tells receiving servers to reject messages from any unauthorized sources.
If your business uses third-party providers, you’ll need to include each service’s SPF records using “include” statements. Common examples include:
- Google Workspace: include:_spf.google.com
- Microsoft 365: include:spf.protection.outlook.com
- Mailchimp: include:servers.mcsv.net
For mixed environments, you can combine different mechanisms into one comprehensive SPF record. For instance:
- v=spf1 include:_spf.google.com include:servers.mcsv.net ip4:203.0.113.1 -all
This example authorizes Google Workspace, Mailchimp, and a specific IPv4 address to send on behalf of your domain.
How to Check Your SPF Record
Verifying your SPF record is an essential step to ensure that it is both correctly configured and functioning as intended. Proper validation helps you catch errors early, long before they disrupt email deliverability or expose your domain to misuse.
A variety of free and reliable tools are available for this purpose. Popular options include MXToolbox, PowerDMARC’s SPF checker, and Google’s Admin Toolbox. These platforms allow you to quickly analyze your published SPF record and return detailed reports. They highlight whether the record is correctly formatted, detect syntax errors, and flag potential DNS lookup problems that could cause unexpected failures.
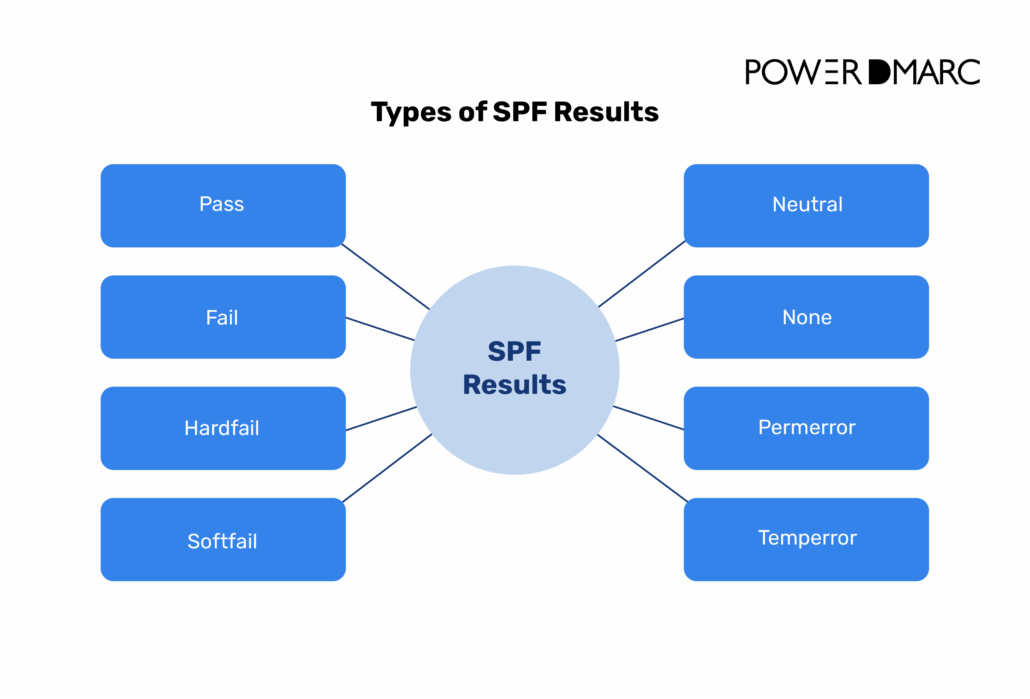
When you run a check, the results will typically display one of several outcomes:
A result of “pass” indicates that the sending server is authorized and the email has successfully met SPF requirements. A “fail” result means the server is not listed in your SPF record and the email is considered unauthorized.
A “softfail” suggests the server is likely unauthorized, but the email may still be delivered (often with a warning or sent to the spam folder), and a “neutral” result means the SPF record has made no clear statement about whether the server is authorized, leaving the decision up to the recipient’s mail server.
In addition to these, there are other possible outcomes. “None” means no SPF record was found for the domain, so there is no published policy to validate against. “Permerror” (permanent error) occurs when the SPF record is invalid or misconfigured, for example, if there are too many DNS lookups or syntax errors, making it impossible for the recipient server to evaluate it properly. “Temperror” (temporary error) indicates a temporary problem, such as a DNS failure, that prevented proper SPF validation but may be resolved by retrying.
Common SPF Mistakes to Avoid
While SPF provides powerful protection, it is easy to undermine its effectiveness through misconfiguration. Understanding these mistakes helps you implement more effective SPF records from the start.
The most significant error is creating multiple SPF records for a single domain. According to SPF limitations, DNS only allows one SPF record per domain. If more than one exists, receiving servers may treat the record as invalid, causing legitimate emails to fail authentication. Instead, all authorized sending sources must be carefully consolidated into a single, comprehensive record.
Another common problem arises from exceeding the 10 DNS lookup limit. Each “include” statement or mechanism that references external DNS entries counts toward this limit, and complex setups can surpass it without careful planning. When this happens, SPF validation fails by default, undermining both deliverability and trust.
A further oversight is failing to update SPF records when changes occur in your email infrastructure. For example, if you adopt a new marketing platform, switch hosting providers, or migrate to a service like Microsoft 365 or Google Workspace but neglect to update your SPF record, your legitimate messages may begin to fail authentication. This disrupts business communications and can harm customer relationships if critical emails do not arrive.
The Bottom Line
The type of SPF record you require is determined entirely by your email service setup and the overall infrastructure you rely on. If your organization manages its own mail servers, your SPF record must include the corresponding IP addresses. If you depend on third-party providers such as Google Workspace, Microsoft 365, or specialized marketing platforms, your record needs to incorporate their published mechanisms. In every case, the record should comprehensively list all legitimate sending sources to ensure your domain is fully protected from misuse.
However, it is important to understand that SPF on its own does not provide complete protection. While it validates sending sources, attackers can still bypass SPF by spoofing the visible From: address, tricking recipients into believing an email comes from your domain even if it fails SPF checks.
This is why SPF should never operate in isolation. Pairing it with DKIM (which validates the integrity of the message) and DMARC (which enforces alignment between the visible sender and authentication results) creates a true multi-layered defense. This combined approach significantly strengthens your protection against phishing, spoofing, and domain abuse, while also giving recipients greater confidence that your messages are authentic and trustworthy.
If you’d like expert guidance tailored to your setup, consider booking a demo with PowerDMARC to see how our solutions can help you secure your domain more effectively.
Frequently Asked Questions (FAQs)
What happens if I don’t set up an SPF record?
Without an SPF record, your emails are far more likely to be flagged as suspicious or marked as spam by receiving mail servers. More critically, cybercriminals can easily spoof your domain, sending phishing or fraudulent emails that appear to come from your organization. This not only jeopardizes your email deliverability but also puts your brand reputation and customer trust at significant risk.
Can a domain have multiple SPF records?
No, domains should have only one SPF record. Multiple SPF records violate the standard and cause authentication failures, as mail servers will be unable to interpret which record is authoritative. Instead, combine all authorized sources into a single record.
- Employee Phishing: Risks, Examples & Prevention Tips - December 15, 2025
- Locky Ransomware: Stay Protected From Email Threats - December 11, 2025
- Top 9 DMARC Providers in the Market - November 30, 2025